


Next: Summary
Up: Tiger: A Fast New
Previous: Specification
- The nonlinearity comes mostly from S-boxes from 8 bits to 64 bits. This
is much better than merely combining additions and XORs (i.e., using the carry
bits), and it affects all the output bits, not just neighboring bits.
- There is a strong avalanche, in that each message bit affects all the
three registers after three rounds --- much faster than in any other hash
function. The avalanche in 64-bit words (and 64-bit S boxes) is much faster
than when shorter words are used.
- As remarked above, all shortcut attacks on MD*/Snefru target one of the
intermediate blocks. Increasing the intermediate value to 192 bits helps thwart
these attacks.
- The key schedule ensures that changing a small number of bits in a
message affects many bits during the various passes. Together with the strong
avalanche, it helps Tiger to resist attacks similar to Dobbertin's differential
attack on MD4 (where changing certain bits in the message affects at most two
bits in many rounds, and then these small differences can be made to cancel out
in the last pass).
- The multiplication of the register b in each round also contributes
to the resistance to such attacks, since it ensures that bits which were used
as inputs to S boxes in the previous rounds are mixed into other S boxes as
well, and to the same S boxes with a different input difference. This
multiplication also prevents related-key [B94] attacks on the hash function,
since the constant differs in each round.
- The feedforward prevents meet-in-the-middle birthday attacks that find
preimages of the hash function (although their complexity would be
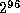 anyway).
anyway).
Eli Biham
Thu Feb 8 15:00:23 IST 1996
 anyway).
anyway).



 anyway).
anyway).